The LARUS Experience with Keycloak
Application security is one of the most important topic these days in the IT world. Any unauthorised access to confidential information can put the company hosting the data through major financial and legal penalties.
What modern companies want is access to reliable and possibly easy-to-use tools that manage which users can actually identify and access their applications.
This article will be about one of these tools, which you’ve probably already guessed from the title, Keycloak.
💡 The goal of this article is to answer the main questions that arise in everyone’s mind when choosing Keycloak: What does it offer? Is it the actually the best solution for my use case?
What is Keycloak?
Keycloak is an open source software product to allow single sign-on (SSO) with Identity and Access Management (IAM) aimed at modern applications and services.
The project is under Apache License 2.0 and since March 2018 it is developed, funded and maintained by Red Hat. It is also used as an upstream project for Red Hat SSO.
There are currently three major distribution for Keycloak: Server, Docker Image and through Operator SDK. Which one to choose is up to you.
Introduction
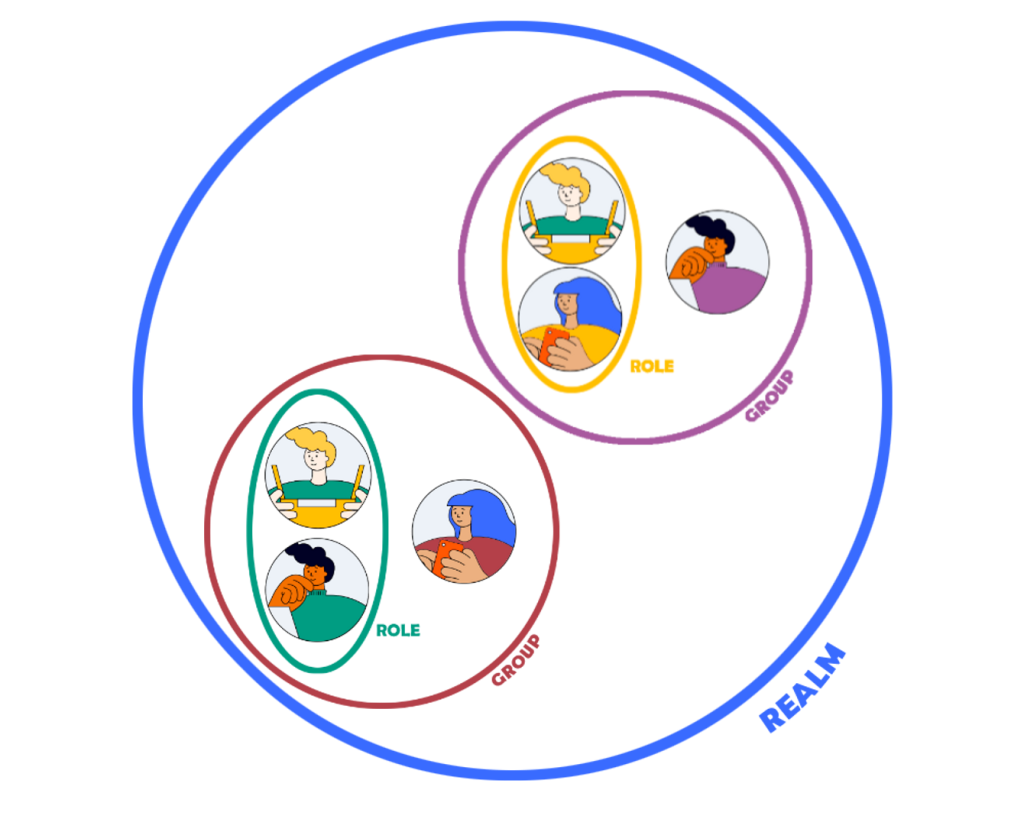
Before looking at the main features that the tool offers, let’s define some core concepts that are the nitty gritty of configuring Keycloak for your application. I will therefore often use them from now on in the article.
Users: Users are entities that are able to log into your system. They can have attributes associated with themselves like email, username, address, phone number, and birthday. You can assign them group membership and make them have specific roles.
Roles: Roles identify a type or category of user. Applications often assign access and permissions to specific roles rather than individual users. In fact, dealing with users can be too fine-grained and hard to manage.
Groups: Groups manage groups of users. You can define a set of attributes for each group. You can also map roles to a group. Users that become members of a group inherit the attributes and role mappings of that group.
Realms: A realm manages a set of users, credentials, roles, and groups. A user belongs to and logs into a realm. Realms are isolated from one another and can only manage and authenticate the users that they control.
Clients: Clients are entities that can request Keycloak to authenticate a user. Most often, clients are applications and services that want to use Keycloak to secure themselves and provide a single sign-on solution. Clients can also be entities that just want to request identity information or an access token so that they can securely invoke other services on the network that are secured by Keycloak.
Keycloak Features
So let’s have a look now at what the tool actually offers.
Multiple Protocols Support
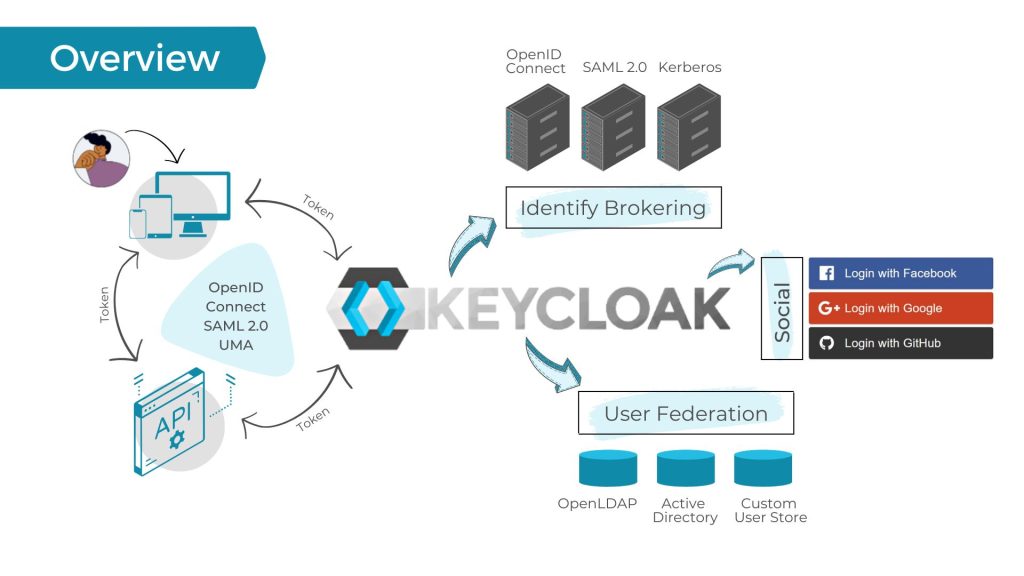
As of right now Keycloak supports three different protocols, which are OpenID Connect, OAuth 2.0 and SAML.
- Single Sign-On & Sign-Out: Allows user to authenticate only once to access several related, yet independent, services.
- Two-Factor Authentication (2FA): Keycloak supports 2FA both via mail and cellphone to add a layer of security to Authentication.
- Admin Console: Keycloak offers a fully customizable GUI where you can manage all configurations required for each separated realm.
User Identity and Access
Keycloak allows you to create users database with custom roles and groups. This can come in handy when you need to grant specific access permission to parts of the application.
LDAP Integration: By default, Keycloak supports LDAP and Active Directory to synchronize with user databases. You can use Keycloak User Storage SPI in case you want to create a custom extension. If you intend to pursue the latter make sure that your solution has all the data that Keycloak requires to be fully functional (See here).
Identity Broker: Keycloak can also work as a proxy between your users and some external identity provider.
Social Login: Keycloak has built-in support for Google, Twitter, Facebook and other famous social media platform. You will still need to perform a little manual configuration for this feature to work properly but for the most part setting up login with third-party services is pretty straightforward.
Pages Customization: Keycloak lets you customize all pages in the Admin Console with themes. You can easily create a custom theme using a classic combination of HTML and CSS and import it into Keycloak. If you want to make things a little spicy you can even include JS scripts.
The list of features that Keycloak offers does not end here. Rather, those are to me the most desirable. If you want to see the list of all the features you can do it here.
Why Use Keycloak?
- First of all, it’s open source, therefore it’s free. I know this may sound cheap (pun intended) but this is actually a good point! Most of the alternatives to Keycloak (AuthO, Okta…) require you to pay and offer similar services.
- You have fully integrated Single Sign-On and Sign-Out, allowing your users to access different applications with a single Login.
- You can manage the applications using different security protocols with just a single tool instead of having one for each client. Keycloak natively supports three different authentication protocols. From a single control point you can handle different security demands by simply splitting your applications in different realms. This also means that you have more freedom when choosing which protocol suits your applications the best, since you know you have no limitations coming from the tool.
- In each realm you can split your users in groups and give permissions to the group instead of the single users. This comes in handy if you need to limit the features that your application can offer. Also, the data that each user can see based on its authority.
- If you already have a user database such as LDAP or Active Directory then configuring Keycloak will be effortless since it has built-in mechanism to synchronize itself with such identity providers.
- Moreover, if you are planning to add a system of Social Login to your application keep in mind that Keycloak supports it out of the box.
Non-technical benefits
- Keycloak documentation on its own is pretty well written. It has step-by-step guides on basically anything that you can think about when it comes down to configuring the tool. Therefore, you can mostly found the answer to your questions there.
- Another advantage of Keycloak is having a big community support. This means that if you can’t sort your problems out by looking at the documentation you can certainly find lots of examples online.
- Lastly, the GUI that the tool offers is well done and user-friendly making any configuration change time saving and easy. Also every part of it, from the Login Screen to the Admin Console of each realm, is fully customisable. This is something that often gets overlooked, but being able to give a tone to your application is always appreciable.
When May Keycloak Not Be The Best Option?
I said at the beginning of this article that we’ll have discussed both why you should use Keycloak and why not. So now I’ll tell you some reasons why you may consider other alternatives. As you may expect, most of these are simply the opposite of the reasons I wrote in the previous paragraph.
You don’t need SSO. If you have a single application then you won’t use Keycloak to its fullest since you won’t benefit from Single Sign-On and simply need a portal to Login to your client.
No integration with any other user data provider. If you have a pure user database containing only usernames and credentials and you don’t plan to give special permissions based on role, group… then Keycloak may overcomplicate what you are trying to achieve.
You prefer to have some sort of guarantees that open-source projects like Keycloak usually don’t offer. You don’t have a road map and in case something doesn’t work as intended you can surely open a new issue on their GitHub. By doing so, however, you have no clue on when they will take your request in charge to solve your problem.
❕ This last point is usually true for open-source projects therefore i brought it up, but keep in mind that, as I said in the beginning, Keycloak is also being used as an upstream project for Red Hat SSO so you can rest assure that is a well written, well designed system.
I just want to say that meeting any of the conditions above does not preclude you from using Keycloak, it only means that you could use a simpler less demanding solution.
Conclusion
In this article we had a look at Keycloak, what it is, what it can offer and when you should use it. Hopefully I was able to give you some general knowledge on the tool itself and also helped you in deciding if it can actually be a convenient solution for your application.